UUID Generator
The UUID Generator tool allows you to create unique UUIDs (Universally Unique Identifiers) instantly, providing reliable and standardized identifiers for your applications and databases. This tool is perfect for developers, database administrators, and anyone who needs to generate UUIDs for various purposes. The process is quick and efficient, ensuring you get high-quality UUIDs every time.
Share on Social Media:
Efficient UUID Generator: Your Solution for Unique Identifier Creation
In the intricate web of digital systems, creating unique identifiers is non-negotiable. This is where a UUID generator steps in, providing an essential tool for developers and system administrators alike. Here, we explain how to utilize these generators, ensure your identifiers are unique, and navigate the various generations of UUIDs with ease. Embark on a clear-cut journey to maintaining distinctness in your digital endeavors.
Key Takeaways
Universally Unique Identifiers (UUIDs) are critical in ensuring the unique identification of elements in digital systems, using 32 hexadecimal characters structured in a specific format to avoid duplication.
There are different versions of UUIDs, each tailored for specific use cases, with version 4 UUIDs standing out due to their high randomness and low collision rate, generated through random or pseudo-random numbers.
UUIDs have practical applications in software development, particularly in user management and distributed systems, ensuring uniqueness and integrity of data; employing best practices and understanding security and performance implications are vital when using UUID generators.
Exploring the Role of UUIDs in Computer Systems
In the digital world, distinctness is paramount. UUIDs, or Universally Unique Identifiers, aptly fulfill this requirement as a form of namespace identifier. Their widespread adoption underlines their crucial role in precisely and reliably pinpointing each element within a system. From operating systems to database keys, and system identification, UUIDs are the unsung heroes that ensure the smooth running of the vast digital landscape.
Their integral reliability in distributed systems that power daily applications underscores their indispensable role in computer systems utilizing Microsoft technologies.
What is a UUID?
A UUID is more than a string of characters; it’s a universally unique identifier designed to generate unique identifiers with a standard that ensures each is a one-of-a-kind treasure within the digital universe. Consisting of 32 hexadecimal characters divided into five groups by hyphens, a UUID is a meticulously structured code. It adheres to a specific format and generation process that may involve the use of random or pseudo-random numbers, adding an extra layer of complexity and security. This unique identifier, also known as a term guid, follows a precise system to maintain its uniqueness.
Far from being a random assembly, this framework is a calculated creation complying with established standards, including RFCs, which guarantees its technical soundness.
The Significance of Uniqueness
Why is uniqueness such a prized attribute in computer systems? The answer lies in the potential for conflict and confusion that arises when multiple objects or users claim the same identifier. UUIDs offer a solution by providing a unique identifier that can be generated independently and combined into a single database without the fear of duplicate identifiers. This unparalleled ability to uniquely identify information allows for an ecosystem where various components, despite being created separately, can coexist and collaborate without issue.
This significant element of uniqueness transforms potential overlap chaos into an organized, conflict-free system.
Delving into the Different UUID Versions
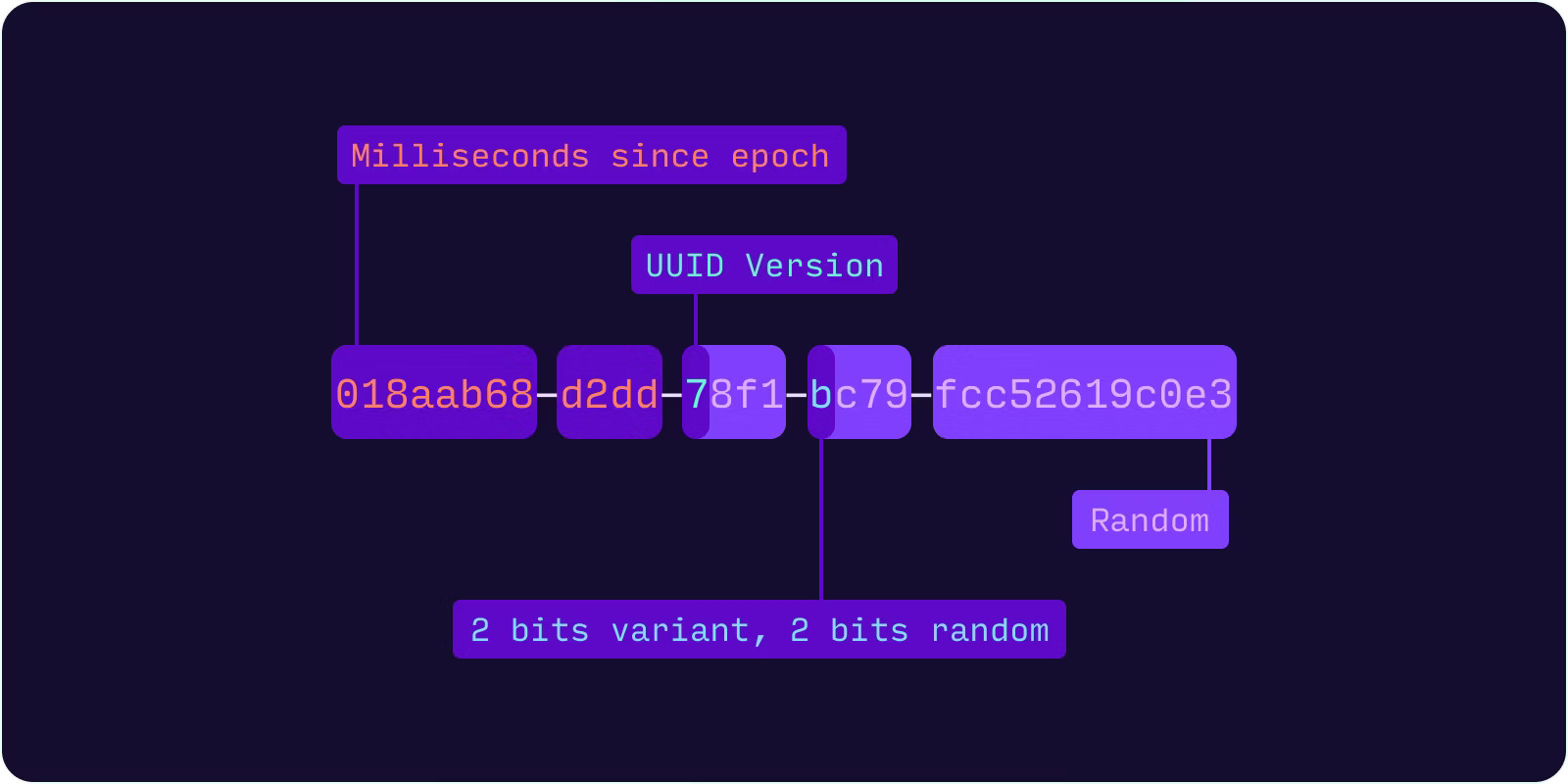
As we delve deeper into the world of UUIDs, we encounter several versions, each with its unique method of generation and purpose. The version 4 UUIDs stand out for their use of random numbers, which ensures a very low collision rate and high uniqueness. In fact, the version 4 uuid is considered one of the most reliable methods for generating unique identifiers.
UUIDs’ versatility shines through each version, tailored to meet specific needs and contexts, from legacy systems to modern applications requiring high randomness and robust unique identifiers.
The Mechanics of Version 4 UUIDs
Diving into the mechanics of version 4 uuids reveals their reliance on random or pseudo-random numbers, earning them the moniker of random UUIDs. The randomness is not just for show; it’s the cornerstone of their strength in generating uuids that are truly one of a kind. By employing functions like Python’s uuid4, developers can summon a fresh UUID with the assurance of minimal collision risk and maximal uniqueness, making them an ideal choice for software programs and database records where singularity is essential.
The low collision probability of this method is by design, not by chance, ensuring each generated UUID can confidently claim its own space without infringing on others.
Legacy and Specialized UUID Versions
Beyond the randomness of version 4, there exist legacy and specialized UUID versions, each with a history and purpose. Versions 3 and 5 bring hashing into the mix, utilizing algorithms like MD5 and SHA-1 to generate uuids based on predetermined names and namespaces.
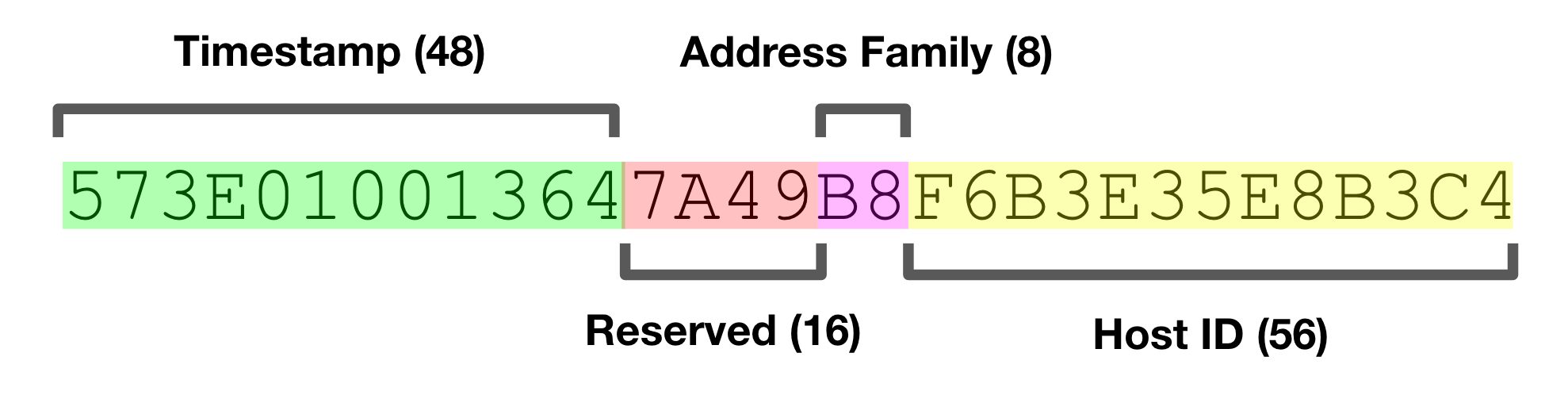
While version 2 UUIDs mingle timestamp and MAC addresses in their creation process, their irregular standardization makes them less common in today’s applications. In contrast, version 3 UUIDs ensure interoperability across systems by generating the same UUID for the same namespace and name combination when hashed with MD5, a nod to their legacy roots that do not rely on a mac address.
Generating UUIDs: Tools and Techniques
In the quest to generate unique identifiers, a plethora of tools and techniques stand at the ready. Online generators and programming languages offer a suite of options for those seeking to create UUIDs. Server-side generation is particularly notable due to its use of robust algorithms, ensuring the generated UUIDs are sturdy and resilient.
PagesTools.com's UUID Generator
In the realm of online generation, PagesTools.com’s UUID Generator stands out for its efficiency in creating random UUIDs. This tool is engineered with precision to specifically generate version 4 uuids, which are lauded for their high randomness and minimal collision risk, making the process of generating uuids an effortless venture.
Customizing UUID Generation
For those who seek to tailor their UUIDs to specific requirements, the world of programming, particularly Python, offers a playground of possibilities. Custom UUID generation can be achieved with modules that provide URL-safe, base64-encoded UUIDs, offering a more compact and web-friendly representation.
Python’s configurable functions offer developers the flexibility to generate unique identifiers in custom formats, catering to specific patterns and use cases. This showcases the adaptability of UUIDs when used creatively.
Practical Applications of UUIDs in Software Development
UUIDs are not just theoretical constructs; their practical applications in software development are vast and vital. From the authentication of users to the unique identification of database records, UUIDs are the linchpins that maintain order and integrity within the digital realm. They enable developers to navigate the complexities of data management with confidence, knowing that each piece of information can be tracked and managed without the specter of duplication looming overhead.
UUIDs in User Management
In the domain of user management, UUIDs shine as indispensable tools for ensuring that each user is as unique as their digital fingerprint. Their role in systems, particularly ecommerce platforms, is critical in differentiating one user’s account from another, safeguarding the authenticity and personalization of the user experience.
This unique identifier becomes a key to a realm of personalized content and secure transactions, standing as a testament to the power of UUIDs in managing digital identities.
Managing Data Across Distributed Systems
When data is scattered across multiple nodes in distributed systems, UUIDs serve as the harmonizing force that ensures consistency and identifiability without the need for central oversight. Each node can independently generate unique identifiers, bolstering the performance and scalability of the system as a whole.
The use of UUIDs mitigates the risk of ID collisions across nodes, which is critical for maintaining the integrity and consistency of the data, regardless of the complexity or scale of the network.
Ensuring Best Practices When Using UUID Generators
Following best practices when using UUID generators is not only recommended, it’s crucial for upholding system security and efficiency. Here are some key steps to follow:
Employ cryptographically secure random number generators to shield UUIDs from prying eyes and potential exploits.
Prevent unauthorized access to UUID generation methods.
Keep source algorithms private to safeguard the integrity of our systems.
By following these best practices, you can ensure the security and efficiency of your UUID generation process.
Security Considerations
Security considerations take center stage when generating UUIDs. Cryptographic PRNGs, as recommended by RFC 4122, provide the necessary randomness and security to ensure that each UUID stands strong against attempts at duplication or prediction. However, not all randomness is created equal; statistical PRNGs can fall short, leading to higher collision risks and compromised security.
Avoiding client-generated UUIDs is key as they may lack the robustness of server-side generation and potentially leave room for vulnerabilities.
Performance Implications
The performance implications of using UUIDs cannot be overlooked. With 16 bytes of storage space per UUID, the potential for increased storage demands and slower database operations is a concern to be addressed. However, by employing frameworks that support sequential UUIDs, such as Comb GUIDs, and optimizing indexing strategies, we can alleviate the burdens of storage and index fragmentation.
Balancing the uniqueness of UUIDs with the streamlined performance of our systems is a critical task.
Navigating Potential Pitfalls with UUIDs
Despite the many advantages of UUIDs, it’s crucial to be aware of potential pitfalls that may accompany their use. Collision, although rare, can occur when the same UUID is generated more than once, posing a risk to system integrity.
Cryptographic techniques and decentralized system designs become our allies in mitigating these challenges, ensuring that UUIDs continue to serve as reliable identifiers.
Collision Probability and Risk Assessment
The likelihood of a UUID collision is exceedingly low, similar to finding a needle in a haystack, even after generating 103 trillion version-4 UUIDs. However, the devil is in the details, and utilizing cryptographically secure random number generators is vital for minimizing the risk of duplication and ensuring that random uuid retains their integrity.
The dangers of statistical PRNGs are not to be underestimated, as they can inadvertently increase the likelihood of collisions and make UUIDs more predictable, a significant security concern that users should be aware of at their own risk.
Compatibility and Integration
The true value of UUIDs is their universal compatibility and the ease with which they integrate across various platforms and technologies. Whether it’s within the sophisticated confines of an operating system like Solaris or across a multitude of software systems, UUIDs are designed to operate seamlessly. This design philosophy ensures that UUIDs can adapt to a wide array of use cases, from the most specialized to the most common, all the while maintaining their promise of uniqueness and reliability.
Summary
As we reach the conclusion of our exploration, it’s clear that the world of UUIDs is both vast and nuanced. From their roles in ensuring uniqueness across systems to the varied methods of generation and practical applications in software development, UUIDs are foundational to the modern digital infrastructure. By embracing best practices and understanding potential pitfalls, developers and system architects can harness the full potential of UUIDs to create secure, efficient, and reliable systems. Let the knowledge of UUIDs empower you to craft digital solutions that stand the test of time and scale.
Frequently Asked Questions
What is the primary use of UUIDs in computer systems?
UUIDs are mainly used as globally unique identifiers to prevent conflicts in applications such as operating systems, database keys, and system identification. They help ensure uniqueness and prevent duplication.
How are Version 4 UUIDs generated?
Version 4 UUIDs are generated using random or pseudo-random numbers, ensuring a high level of randomness and minimal chance of collisions.
Can UUIDs be customized for specific use cases?
Yes, UUIDs can be customized for specific use cases using programming languages like Python, allowing for URL-safe, base64-encoded UUIDs and other custom patterns.
What are the security considerations when generating UUIDs?
When generating UUIDs, it is important to prioritize security by using cryptographic PRNGs for entropy and avoiding client-generated UUIDs for secure practices. Avoid potential security risks.
Are there any performance implications when using UUIDs?
Yes, using UUIDs can have performance implications due to their storage space requirements and potential for index fragmentation, but these can be mitigated with optimized indexing and sequential UUIDs.